Blockchain for Simple People (Like Me)
Posted by Andrew Prokop on May 17, 2018 10:40:14 AM
"Whoever is careless with the truth in small matters cannot be trusted with important matters."
—Albert Einstein
We’ve all heard the old saying, “Be careful of the company you keep.” This is true for both people and technology. Consider blockchain. For many Americans, the immediate word association is “Bitcoin.” In fact, I would venture to guess that quite a few people think that they are one and the same. While this connection might be favorable for Bitcoin, it has become a bit of a boat anchor for blockchain.
While it is true that blockchain was invented to provide a secure transaction ledger for cryptocurrencies, it has subsequently been considered for everything from personal identification to crowd funding. A quick Internet search took me to sites that discuss how blockchain can be applied to marriage licenses, insurance premiums, and smart appliances. Clearly, while it may have its roots in Bitcoin and “funny money,” thinking of it as Bitcoin is both limiting and deceiving.
For Example:
If you are a little confused by how blockchain works, consider this very non-technical example.
Take a piece of paper and write the words “I love my job” on it. Put your signature underneath this declaration of career joy. Hand that paper to one of your coworkers. Have that coworker change the word “love” to “hate” and turn the paper over to your boss. Without any additional information, your boss might start the process of reassigning you to a different department.
Now, repeat the process, but this time create ten pieces of paper with “I love my job” and your John Hancock. Pass those papers to ten different people. This time, when the evil coworker changes “love” to “hate,” the damage is isolated to a single note and you have nine other pieces of evidence to prove that foul play has taken place.
While blockchain is more involved than that, it is essentially a process of creating validated blocks (those “signed pieces of paper”) and then distributing them to a decentralized, public ledger (those “ten different coworkers”). So, not only does a bad actor have to compromise the integrity of one entry (which through the use of a cryptographic hash is not very easy to do), he or she would have to find and alter every copy of the entry. This makes blockchain ideal for any situation where being completely assured of the veracity of data is essential.
Let’s Get Geeky
A block consists of a chain of validated transactions that are hashed and encoded into a Merkle tree. Each block uses a cryptographic hash of the prior block in the blockchain. This binds blocks together in such a way that altering one block invalidates the binding and thereby, the validity of the chain.
Another layer of integrity is added when storage of the blocks is decentralized. Instead of one single copy of the data, blocks are replicated across multiple servers. Every server that holds a block must approve any changes to the chain. If a change is not approved, the transaction is denied and truth wins out.
This decentralization means that no “official” copy of the data exists and no single copy is trusted more than any other. Not only does this make hacking significantly harder, it eliminates the problem of a single point of failure.
Pictorially, a blockchain transaction looks like this:
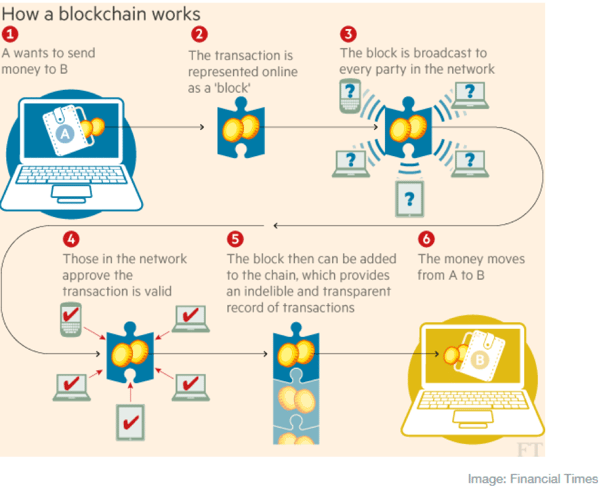
Notice how the network of blockchain servers is accessed when a chain is queried and when a new block is inserted.
Making it Real
I live in the world of communications, so I tend to look at everything from that standpoint. My first reaction to blockchain was, “Where would I use that in my Avaya, Cisco, NEC, Mitel, etc. system?” Is my configuration data begging for this technology? Would I use blockchain to log into a SIP phone? Do I need this level of security when I make a video call?
Clearly, these bread and butter “PBX” scenarios aren’t a very good fit.
However, when I turn my attention to contact centers and those elements of communication that involve customer relationships, it starts to make sense. I can clearly envision how blockchain could be used to properly identify a customer while properly securing his or her interactions and transactions. I can also see how it would be useful in monitoring and acting upon trends gathered from multiple sources. Knowing that my data is 100% trustable can make the difference between right and very wrong choices.
A Solution Looking for a Problem
As the psychologist Abraham Maslow famously said in 1966, "I suppose it is tempting, if the only tool you have is a hammer, to treat everything as if it were a nail." Here in 2018, it’s easy to apply that thought to blockchain. As secure as it makes data storage and retrieval, it comes with a price. In fact, it comes with several prices–performance issues, implementation complexity, a lack of immutability, the potential for restrictive regulation, and reliance upon widespread adoption.
Blockchain is a relatively new technology and while the buzz is currently very high, buzz is never a solution. That’s not to say that enterprises should not be looking at blockchain, but they shouldn’t approach it wearing rose colored glasses. The trick will be to properly identify the problem(s) you are trying to solve and lay all the “right” choices on the table. Remember, just because you can doesn’t mean that you should.
Mischief Managed
I have only scratched the surface of what blockchain is and how you need to look at it. If this is of interest to you (and it most likely should be), I highly suggest that you poke around the Internet for longer and more in-depth discussions. Don’t be blinded by the blockchain hype, but at the same time, don’t be ignorant of what might be a truly revolutionary technology.
[WEBINAR] 3 Steps to Combat Ransomware
May 24 | 12 P.M. (EDT)
ConvergeOne's industry experts will teach you three critical steps toward combating ransomware on our upcoming webinar. The team will showcase how recent ransomware attacks have become so successful at breaking down the barriers of even the largest organizations and what you can do to avoid becoming a victim.
Topics: Security
.jpg?width=120&name=Andrew-Prokop-ArrowSI-0012(1).jpg)


